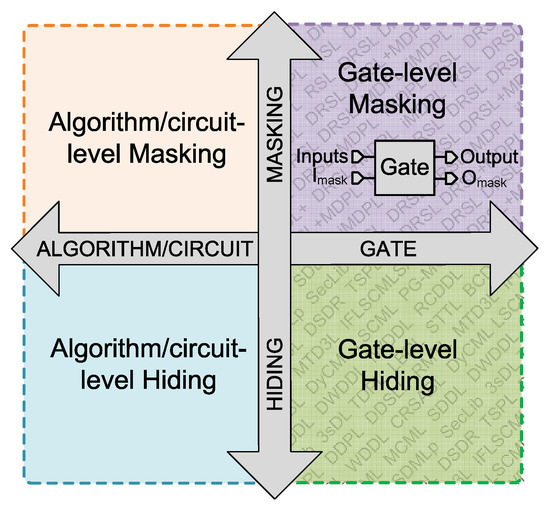
Applied Sciences | Free Full-Text | Gate-Level Hardware Countermeasure Comparison against Power Analysis Attacks

PDF) A Presentation on VEST Hardware Performance, Chip Area Measurements, Power Consumption Estimates and Benchmarking in Relation to the AES, SHA-256 and SHA-512.
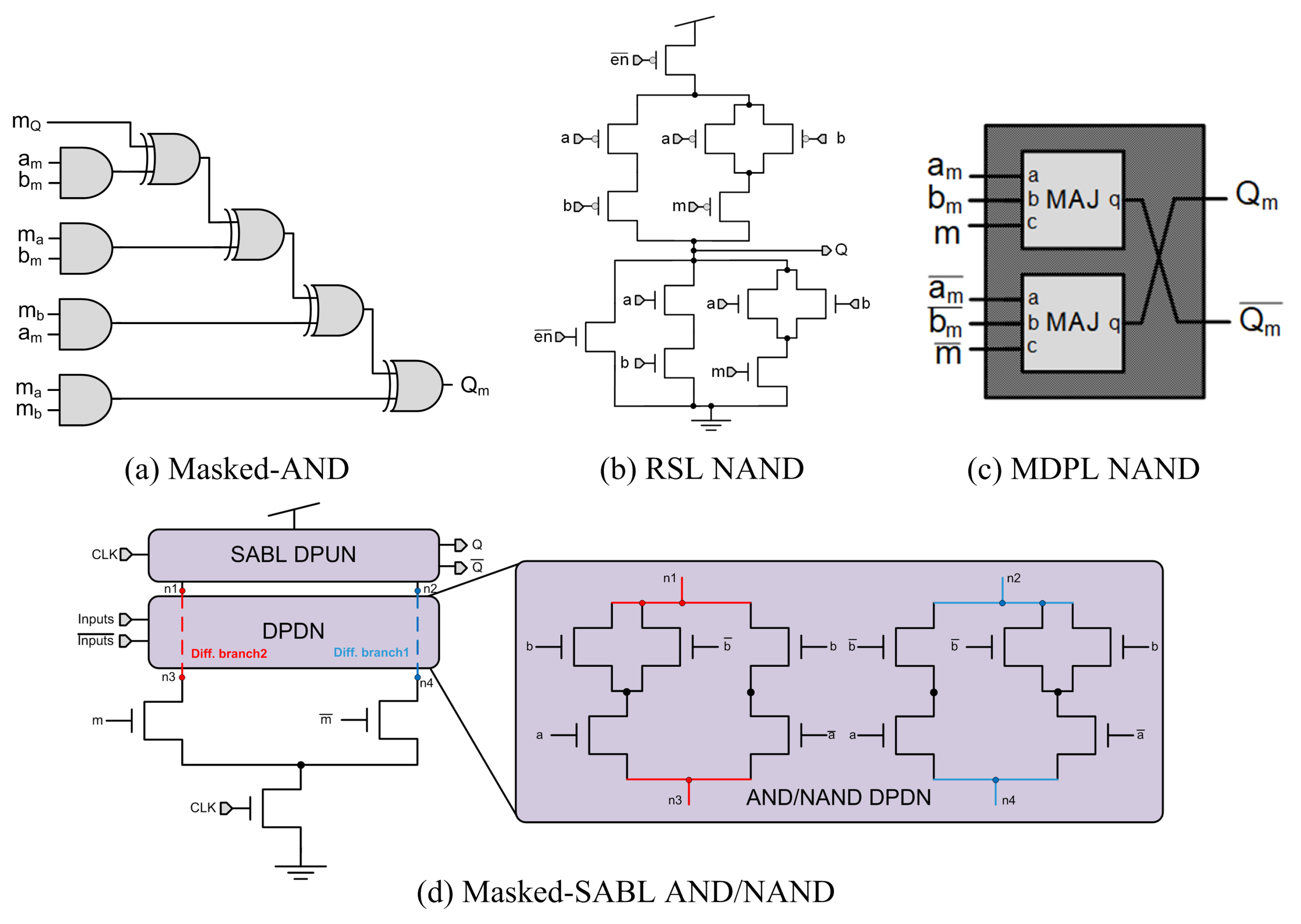
Applied Sciences | Free Full-Text | Gate-Level Hardware Countermeasure Comparison against Power Analysis Attacks
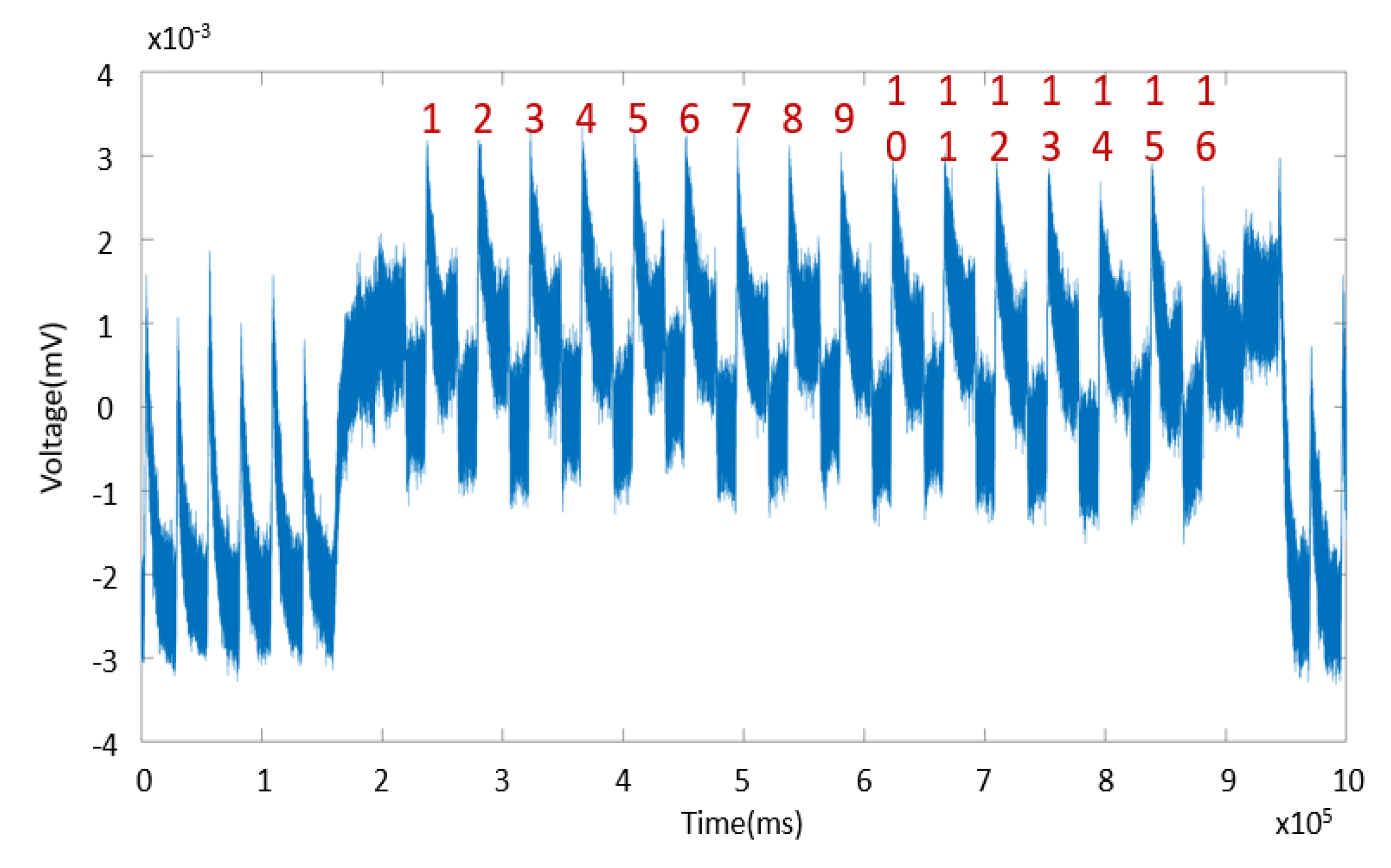
Cryptography | Free Full-Text | Power Side-Channel Attack Analysis: A Review of 20 Years of Study for the Layman